How can I change my password?
You can reset your password on the page serviceportal.math.uni-paderborn.de. To do this, log in on the linked page with your current login data.
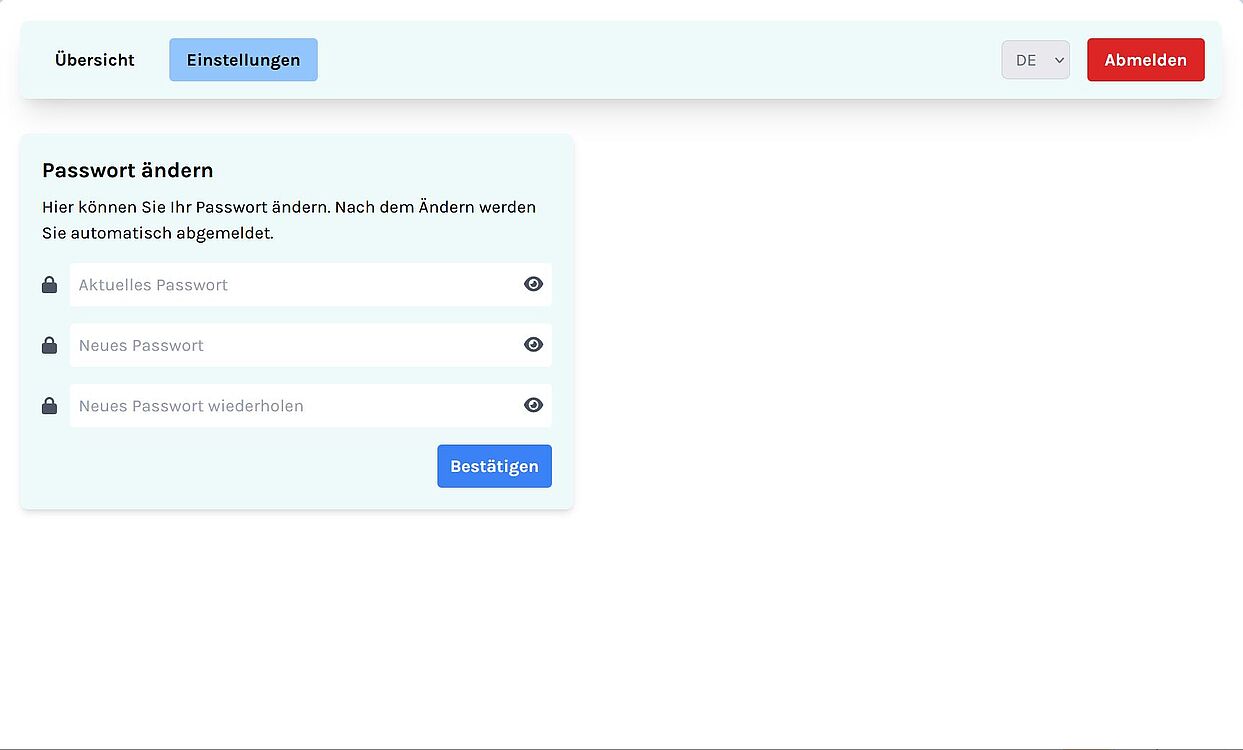
Select the "Settings" tab, Enter your old password in the upper field and the new password in the two lower fields. Complete the process with the "Confirm" button.
What is Kerberos?
Kerberos is an authorisation service with which users, computers or services can authorise themselves to other users, computers or services. It supports encrypted connections and enables single sign-on: a user only has to enter their password once during the entire session. In addition to symmetric cryptography, Kerberos uses a so-called ticket-based procedure. Tickets are electronic ID cards that users and computers use to identify themselves to each other. When a user logs on to the system, they receive - in simple terms - a ticket with which they can identify themselves to all of the system's services (such as ssh or IMAP).
kpasswd - How do I change my password?
To change your own password, Kerberos provides the command 'kpasswd'. In order to change the password, a person must already have a valid Kerberos ticket. Normally (e.g. after logging in) this is the case, so a simple 'kpasswd' is sufficient:
| $ kpasswd Password for dhilbert@MATH.UNI-PADERBORN.DE: Enter new password: Enter it again: |
klist - How can I find out which tickets I currently have?
To display a list of all currently valid tickets, use the 'klist' command:
| $ klist Ticket cache: FILE:/tmp/krb5cc_56510_3pfHET Default principal: dhilbert@MATH.UNI-PADERBORN.DE Valid starting Expires Service principal 28.06.2019 10:41:43 28.06.2019 20:41:43 krbtgt/MATH.UNI-PADERBORN.DE@MATH.UNI-PADERBORN.DE renew until 29.06.2019 06:41:43 |
kinit - How do I get new tickets?
Tickets are generated automatically as long as a person has a "Ticket Granting Ticket" - a kind of general ID card with which a person can identify themselves universally. This ticket is generated the first time you log in, but only lasts for 10 hours for security reasons. After that, it becomes invalid. To request a new ticket granting ticket, use the command 'kinit':
| $ kinit Password for dhilbert@MATH.UNI-PADERBORN.DE: |
The new ticket granting ticket has a lifetime of 10 hours again. After that, a new one must be requested if required.
kdestroy - How do I destroy tickets?
Sometimes it makes sense to invalidate your own tickets, e.g. if you leave the computer and want to be on the safe side. The 'kdestroy' command is available for this purpose:
| $ kdestroy |
What is Secure Shell?
ssh stands for secure shell and is a programme for logging on to a remote computer and executing commands. ssh offers secure encrypted communication even over an insecure network.
Together with ssh, the programme scp is installed in the mathematics network, with which files can be copied between two computers in encrypted form. (Further information can be found below in the explanation of "Alternatives to ftp").
How do I use ssh?
You can use ssh within the maths networks without any further preparation. The following command establishes an encrypted connection to the kepler computer and wants to log in the user name of the local computer:
$ ssh kepler
If you want to use a different user name than the one on the local computer, you can do this as follows (assuming the user is called user):
$ ssh user@kepler
The remote computer then normally requires the password of the user:in user to be logged in.
For which operating systems is ssh available?
In principle, there is an implementation of ssh for every operating system.
Under Linux, OpenSSH can be used via the terminal with the ssh command.
The PuTTY programme is available under Windows. Microsoft has also included ssh in Windows 10 since version 1809. Similar to Linux, ssh can be used via the command line (cmd) or PowerShell.
How do I create a public-key authentication with ssh?
1. if you do not yet have a $HOME/.ssh directory, you must create one with
cd ~
mkdir .ssh
chmod 700 .ssh
2. to generate a key pair, you must use
gudrun@vieta[~]>>ssh-keygen -b 2048 -t dsa -f identity
to generate a key pair. You will be asked for a password for the key. A password can be entered, but is not mandatory.
gudrun@vieta[~]>>ssh-keygen -b 2048 -t das -f identity
Generating public/private das key pair.
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
Your identification has been saved in /gauss/user/gudrun/.ssh/id_dsa. Your public key has been saved in /gauss/user/gudrun/.ssh/id_dsa.pub.
The key fingerprint is: 0f:9d:ff:48:59:42:71:10:00:f9:09:a8:55:34:ab:8a my key
Two keys are generated.
identity.pub -> public key
identity -> secret key
What alternatives are there to FTP?
With ftp, the data is transported in plain text over the network. Alternatively, you can use scp. The following example copies the file test.txt from the news directory of the local computer to the computer kepler in the home directory of the user user:
user@laptop [~]$ scp test.txt kepler:
Conversely, if the file test.txt is to be copied from the user software from the computer kepler to the current local directory, the command is:
$ scp software@kepler:test.txt
As with the cp command, scp also supports the recursive copying of entire directories with the -r option.
How ssh works
When logging in from computer A to computer B, ssh first checks the so-called host_key. This ensures that computer B is actually computer B and not a computer pretending to be computer B. A file with the name known_hosts is used for this mechanism. Here, ssh first searches for a global, centrally managed file in which the system administrator enters the host_keys after installing the computers. If no entry for the corresponding computer is found there, the local file of the respective user:in under $HOME/.ssh/known_hosts is checked. If the identity of computer B can be verified using these files, computer A and computer B are connected. If host B is still unknown to the system, you will receive the following query:
| The authenticity of host 'kepler.math.uni-paderborn University.de (131.234.116.31)' can't be established. ECDSA key fingerprint is SHA256:X. Are you sure you want to continue connecting (yes/no)? |
Note: The current fingerprints of our servers can be found under Fingerprints. Only connect to servers that you can trust. If you select yes, the host_key of computer B is automatically stored in your personal file $HOME/.ssh/known_hosts. The next time you log on to computer B, the host_key will be known and you will no longer receive the above error message. The connection between computer A and computer B is now established. The next step is to authenticate the user:in. To do this, ssh either uses the public key method or asks for the password. Once authentication is complete, the shell is available.
ssh connection without password entry
If you do not always want to enter your password when using ssh (or scp), you must enter the public key of your ssh-key in the file ~/.ssh/authorised_keys (as one line).
Further information
A detailed documentation of the individual commands can be found in the corresponding man pages.
Safety instructions
Rechnerbetrieb Mathematik endeavours to identify and eliminate potential security risks in the mathematics network at an early stage.
However, it is essential for system security that you carefully protect your own user account, not only in the interest of the security of your own data and your own integrity, but also to keep attackers out of the network.
Below you will find some useful tips to make it more difficult for potential attackers to infiltrate your account:
Please change your password regularly!
To do this, use the kpasswd command under UNIX
Please choose a password that is as good as possible!
A "good" password is a mixture of at least six lower and upper case letters, numbers and special characters. A bad choice for a password is e.g:
- Name/first name of the user
- Surname/first name of family members or friends, as well as names in general, dates of birth, account numbers, insurance numbers, etc.
- Computer names, place names, etc.
- Car makes, car licence plates
- basically any word that can be found in any dictionary, no matter how strange it sounds
- all words mentioned so far backwards
- character strings in the order in which they appear on the keyboard, e.g. "qwerty" or "qwertz"
- Character strings consisting of only one or very few characters
We carry out security checks at regular intervals, which include checking the reliability of your passwords. Users whose passwords are too simple will be noticed and blocked.
It sounds almost impossible to find a password that fulfils these requirements and that you can still remember. However, it's not that difficult. For example: think of a short sentence that you can easily remember, take the first letters of each of these words, add a few numbers/special characters, vary the upper and lower case letters and you have a word that comes very close to meeting the above requirements.
Only work on trustworthy computers!
Do not use your login on computers that you do not fully trust. So-called "keyloggers" can record any input and screen contents.
Do not keep your password near your computer!
A simple glance under the keyboard or in a similar hiding place has enabled many an access.
Do not give your password to anyone else!
Even good friends and acquaintances should not know your personal password. Close friends always have close friends and you can quickly lose control of your data.
Please also remember that you are liable for the actions that occur under your login. In the event of obvious misuse, we will block your user ID.
Use encrypted connections!
When using programmes such as telnet or ftp, all data is transmitted unencrypted and can therefore be read. You should therefore use alternatives such as ssh or scp.
When using an email client, make sure that appropriate encryption is activated for the transfer to the mail server.
When browsing the Internet, only transfer sensitive data in encrypted form (via https).
Always log out!
Please log out when you leave your workplace or lock your computer when you return.
